Posts
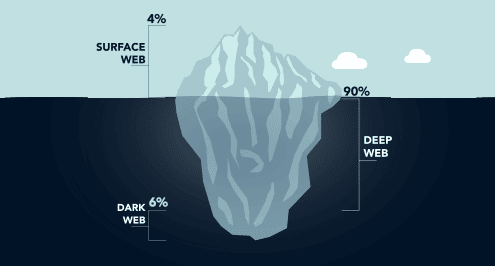
What you need to know about the dark web
Did you know that the "dark web" presents a genuine security threat to your business? It's crucial you understand how the dark web works and why it's a security threat. But even more importantly, you need to know how to protect your business data from the cybercriminals who thrive there.

7 tips for keeping your organization cyber safe
Did you know that cyber vulnerabilities are among the top global threats? You should be concerned about cyber insecurity. But more importantly, prepare your organization, IT infrastructure, employees, and even customers to face every possible cyber threat.
Bringing AI to the cybersecurity arms race
Safeguarding digital assets is now a war of intelligence. Thanks to AI, you can deploy sophisticated systems to automate various IT security processes. But attackers are also responding in kind with smarter threats and tactics. It all comes down to who can outwit the other.

Build a cybersecurity castle for ultimate protection
Sensitive data requires the extra security of a cybersecurity castle. Protect your organization’s reputation and revenue with these seven layers.

Increase productivity with these Chrome extensions
Chrome is the most popular desktop internet browser today, thanks to its ability to load applications, multiple tabs, and web pages with lightning speed. Boost productivity with these Chrome extensions –StayFocused, OneTab, Mercury Reader, Grammarly for Chrome, Ghostery, Todoist, and LastPass.

What is multi-factor authentication (MFA), and why should I use it?
Many businesses, software vendors, and online services are moving away from password-only verification to multi-factor authentication, and you should, too. Passwords are fundamentally flawed and notoriously difficult to secure. MFA makes user identity and access management safer and more dependable.

Minimizing cyber risks with vulnerability assessment and penetration testing
Pentesting vs. vulnerability assessment: which is better? Actually, either one of these processes can give you valuable and actionable insights into any sensitive vulnerabilities lurking with your IT infrastructure. Pentesting and vulnerability testing can work in tandem to mitigate risks.

The importance of business risk assessment
Every business faces perils that might harm its assets, mission, employees, revenue, or reputation. A big part of running a business is all about managing these risks. Conducting a thorough risk assessment shows you all the potential threats to your business and how to handle them.

Tips on how to boost your Wi-Fi signal
There is nothing quite as frustrating as a slow Wi-Fi connection. But you don't have to endure excruciatingly slow speeds when you can easily do something about it. In most cases, it's avoidable problems in the Wi-Fi network that cause sluggish transfers.

Why relying on SMS-based two-factor authentication is a mistake
There is no question about it; 2FA is a far superior identity and access management system than the traditional username-password sign-on. It adds an extra security layer to protect user accounts from password-related hacks. However, 2FA's effectiveness depends on the method and means used.